7 Surprising Statistics That Show Why Mobile-Friendly Websites are a Must for Google!
Is your website mobile-friendly? When a visitor comes to your site using a smartphone or tablet, how does it look? Is it easy to navigate and find...
Protect your organization from evolving threats, ease compliance worry, and have a defense-in-depth approach to security and risk management. We understand security and its role in deploying new technologies, addressing evolving mandates, and combating advancing threats.
{company}’s complete security solution helps reduce security risks, while ensuring the compliance, performance, and management of critical systems and applications. We bring event, threat, and risk data together to provide robust security intelligence, rapid incident response, seamless log management, and extensive compliance reporting.

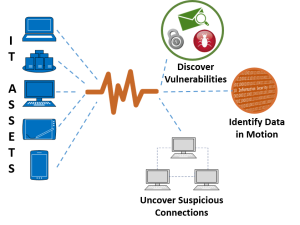
For more information about our Security Platform, contact us


Is your website mobile-friendly? When a visitor comes to your site using a smartphone or tablet, how does it look? Is it easy to navigate and find...
Cybersecurity & Information Security: What Is The Difference? "What is the difference between cybersecurity and information security?" This is not...

On Time Tech is an IT Support and Computer Services company serving California. We provide services to the areas in and around We know businesses like yours need technology support in order to run highly-effective organizations. Leverage pro-growth technology services for your company now.
San Francisco:
182 Howard St.
Suite 108
San Francisco, CA 94105
Los Angeles:
8350 Rex Road
Pico Rivera, CA 90660
Business Hours:
M-F: 8AM-9PM
© 2024 On Time Tech